
|
got a virus? |

|
|---|
PC Technician - Fake FBI notice MoneyPak extortion
|
Fake FBI notice tries to extort money with MoneyPak
Well boys and girls - I finally got caught with a phoney ransomware program. I think it happened when I noticed a website in a list of websites when using the hypestat.com site to check traffic stats for my websites. The site I decided to look at had an unusual name ( sorry can't remember the site name ) and as soon as this site opened - I got some pop-ups so I tried to immediately close all the pop-ups. But alas, I was too late - as a few seconds later I got this ( see screen shot below:) which filled the entire monitor and I could not escape out of this screen except by following the instructions to pay a ransom of $200 to the bozos who infected me. 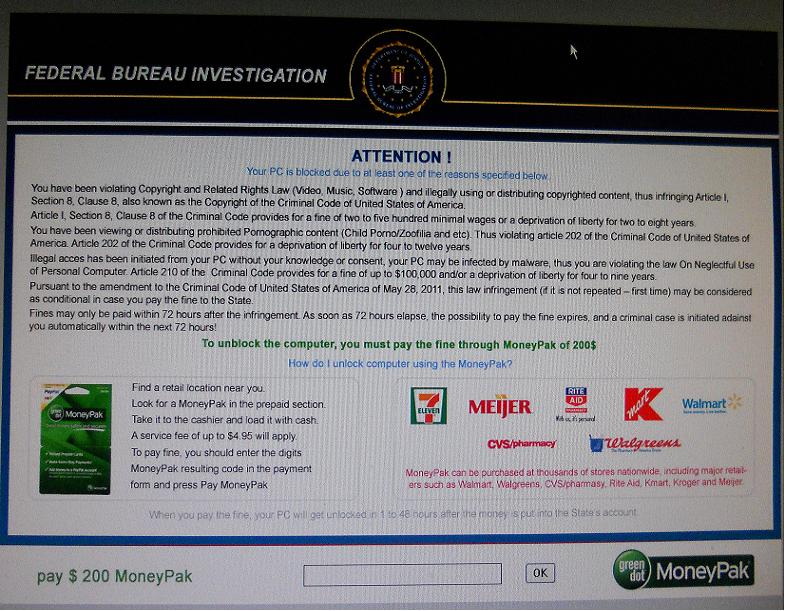
Well no way am I going to knuckle under to this ransom demand. So I did some research and figured out that the ransomware was in the following directory: \document and settings\[user name]\application data\hellomoto This became obvious as the "hellomoto" directory was created the same day the ransomware appeared. My research revealed that since the ransomware requires an internet connection then you should be able to disconnect your ethernet cable and boot to normal startup in windows. Well, yes and no, my machine (Windows XP) wasn't able to boot to the normal desktop ( got the full screen image above ) but my friend who was has the same problem was able to do so - i.e., his windows 7 computer did boot normally. This concept makes some sense as there would be no reason for the ransomware to display the message if there is no internet connection. It must try to detect if an internet connection exists - so if one doesn't exist then there is no sense in displaying the ransom note - how would the victim pay? The point is you can boot in safe mode which I did - and no ransom note appeared. While in safe mode I was able to navigate to the "hellomoto" directory and found two files there 1. BukF.dat 2. TujP.dat Aha! - these must be the culprits. I used notepad to view the contents of these two files. Displayed below are the screen shots of these two. As you can see this looks more like the goobledegook of an executable file ( a computer program ). I did search for some "clear text" to see if I could figure out what these programs do. No such luck - I couldn't find anything. 
I deleted the two files and restarted windows in normal mode. I then ran Malware Bytes Anti Malware ( MBAM) just in case there are other troublesome files. Well, the MBAM ran for 8 hours and then it stopped responding ( not sure why ) so I ended the MBAM program and restarted my computer into normal windows mode. Note however, during the MBAM scan - I got a pop-up from my AVG free program that it detected a threat - this is the "BackDoor.Generic15BYSQ" trojan. See screen shot below: 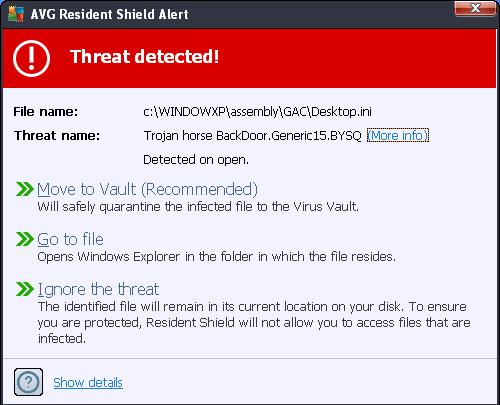
I also got several more threats detected messages - see the screen shot below. Note that the program that opens the trojan ( and tries to execute ) is called "FlashPlayerUpdateService.exe". The Flash Player program is probably just doing its normal thing but since the desktop.ini is corrupt ( it's an executable program ) - the trojan can begin to attack. This arrangement is probably how the attack vector gets started. 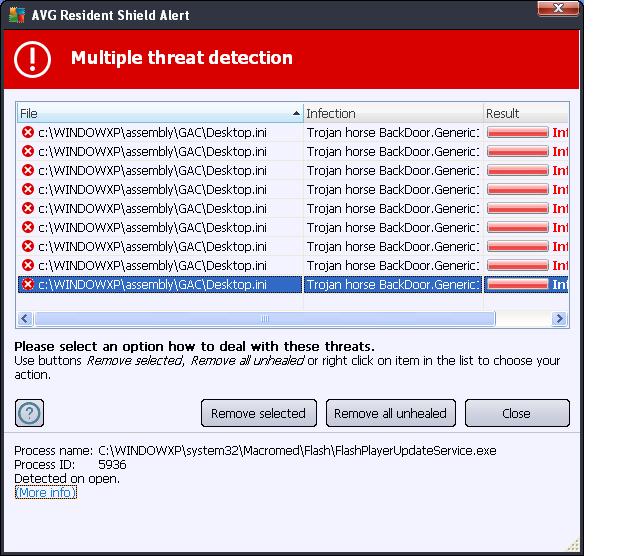
In the screen shot below is another attempt to execute the trojan - this time using GoogleUpdate.exe which is probably a normal event but since the "desktop.ini" is corrupt the trojan can make another attempt to infiltrate my computer. 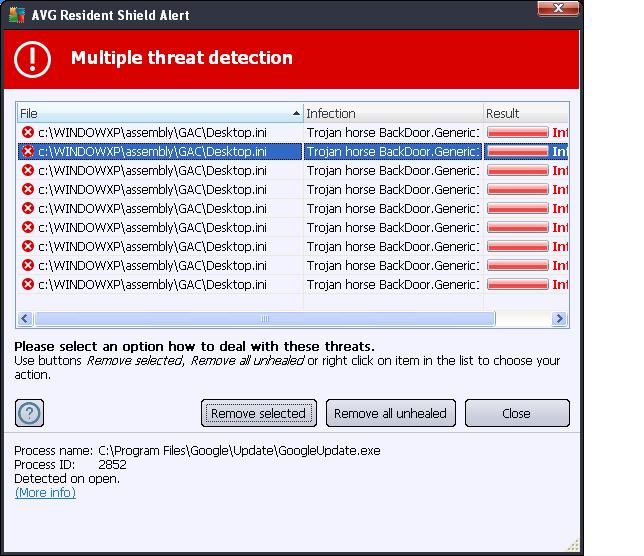
I am not sure if the trojan and the ransomware programs are related so I rebooted my computer using my "Bart PE Builder" bootup disk. I navigated to the "assembly\GAC" directory under my windows directory. I had to change the attributes of the Desktop.ini file using the DOS command attrib -h -s desktop.ini within the Command Prompt window of "Bart PE Builder". I then deleted the "Desktop.ini" file. By the way, the two images below show the code contained within the desktop.ini file. Page one of code: 
Page two of code: 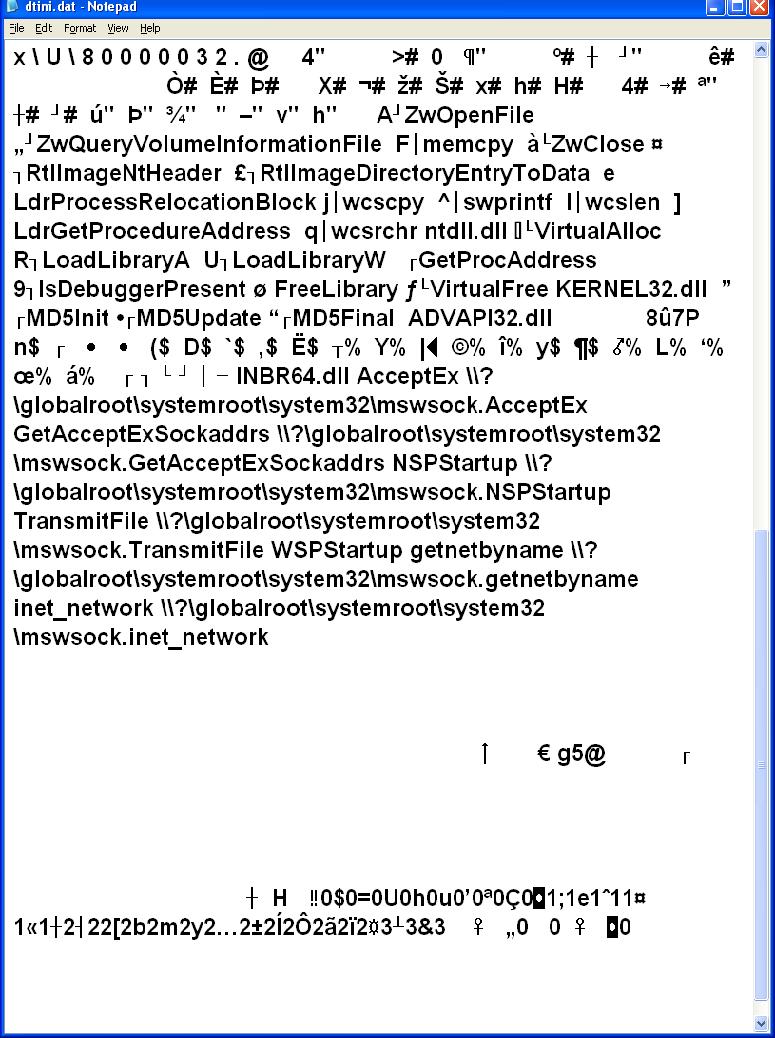
Note that in the two pages of code above that there is some "clear text". I can see some references to mswsock - the windows socket program? One would have to reverse engineer the code to figure out what is going on. So to summarize - I think by deleting the two files in the "hellomoto" directory the ransomware program was eliminated ( so far no pop-up FBI warning screen ). For Windows 7, these two files may be in the directory \Users\[user name]\AppData\Roaming\ Or \Users\[user name]\AppData\Local\Temp Also, it appears that the trojan ( BackDoor.Generic15.BYSQ ) was a separate issue and most likely did not spawn the FBI ransomware program. As of now, all seems to be back to normal. Oops - I spoke too soon - I thought I was finished but when I rebooted my computer - everything came back - the ransomware FBI warning and the GAC/Desktop.ini file. - Yikes. So I booted into safe mode - to avoid the FBI bogus warning. I started the Malware Bytes Anti Malware program - it ran for about 7 hours and then it stopped responding. Apparently, MBAM got hung up in this folder. "\documents and settings\[user name]\local settings\temp" so from safe mode I deleted all files and folders in this ( the temp ) directory. I then loaded "Kaspersky Virus Removal tool" from a CD which contained the setup program for the Kaspersky V.R.T. and let it run. This was suppose to clean up the GAC\Destop.ini trojan but it also cleared up the FBI bogus program as well. Not sure why this happened but maybe the program that spawns the "hellomoto" directory containing the two files "BukF.dat" and "TujP.dat" - the FBI ransomware program was in the "temp" directory. So when I rebooted - the FBI was indeed gone but the GAC/Desktop.ini was still there. Okay now I ran MBAM again - and it ran about 8 hours and reported it had found 7 threats before it "stopped responding" - oh great - I had to kill the MBAM process but I did note that it was searching in the documents and settings folder where it hung up. The trouble with killing the process before completion is that I wasn't able to tell MBAM what action to take to handle the threats. Phooey! So I told MBAM not to search the "documents and settings" folder and started the search again ( I figured I wanted to get through this as quickly as possible - and the threats were found before this folder). Now It stopped again ( after 6 hours at the folder c:\windows ) with MBAM reporting 8 threats. I still couldn't see the threats - as all I could do was to kill the MBAM process. Now I told MBAM to not search "C:windows" and "C:Documents and settings" and ran it again - so it could finish quickly and so I could see the results of the scan. Well, finally it finished ( about 1.5 hours ) See the screen shot below: 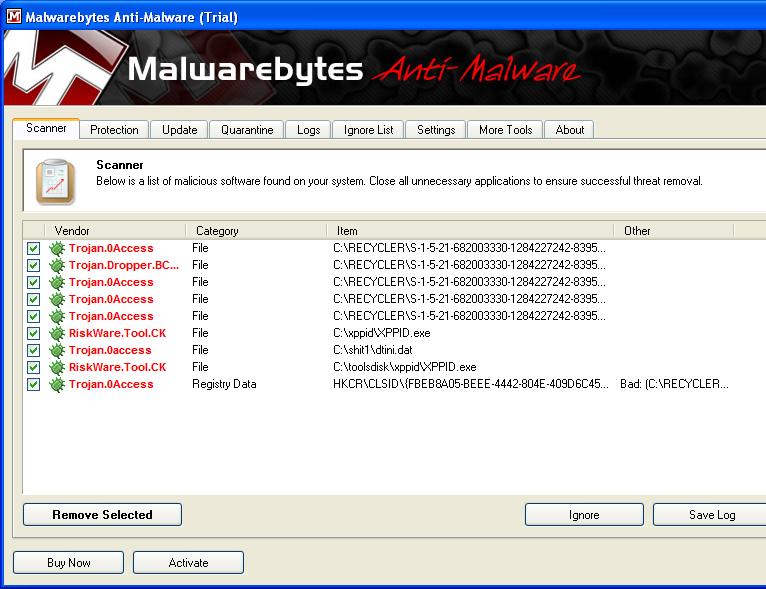
Notice that trojans use the "recycler" directory to hide its dirty work. Also note the directory "shit1" contains a file called dtini.dat - I actually put that there - it is a copy of the GAC\Destop.ini trojan. I then told MBAM to remove the threats. However, after rebooting the GAC\Desktop.ini file was still present. NUTS! So I then ran Kaspersky again - and it looked like this finally worked. Maybe, and this is only a guess, the MBAM progam cleaned out all copies of the desktop.ini file (the trojan.0Access file) so these copies could not be used to re-spawn the Desktop.ini file in the GAC directory. So when the Kaspersky program ran and cleared the desktop.ini file out of GAC - there weren't any more copies to allow a re-spawn. Sorry that this is only a guess - but without a working knowledge of the inner workings of how this all works ( the hackers are a secretive lot ) I can only try to piece this together from the few clues available. One other aside, while I was running the MBAM program - I kept getting a little pop-up window every few minutes. It is shown below: 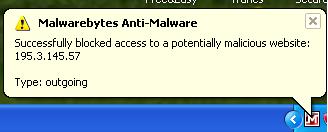
So apparently, some progam is trying to make contact with some malicious web site which can only mean that not all malware ( trojans ) has been expunged. Okay now I ran AVG anti-virus and got the following ( see screen shot below) : 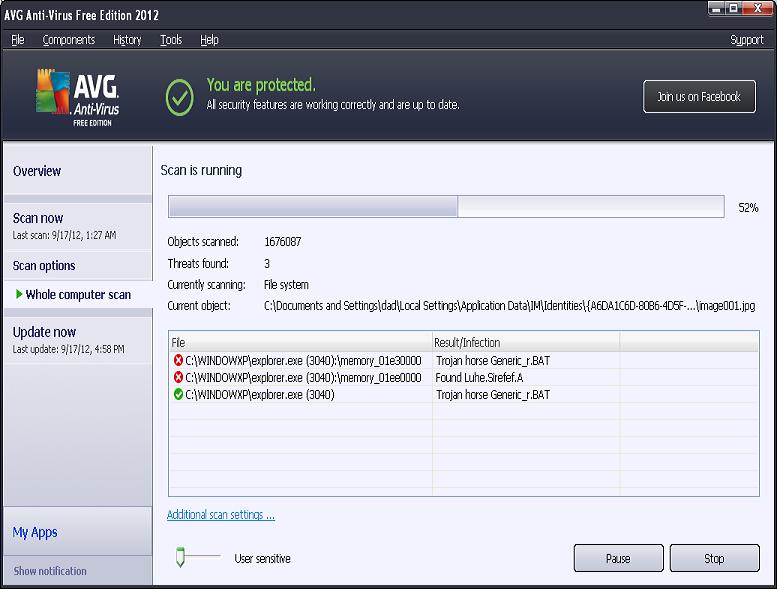
After running AVG - I ran a progam called Taskinfo2003 and looked at the modules in "explorer.exe" - since AVG found threats in explorer.exe. I saw in the modules list for explorer that a file with a name "n" was there. What the hell is this? This has got to be bogus. It doesn't even have a "dll" extension. So I tried to let AVG remove the three threats but it had trouble removing them. So I closed AVG. A few minutes later I got a pop-up from AVG - "threat detected" which was removed successfully - see screen shot below ( note the name of the file - ie, "n" - in the recycler\... directory) . 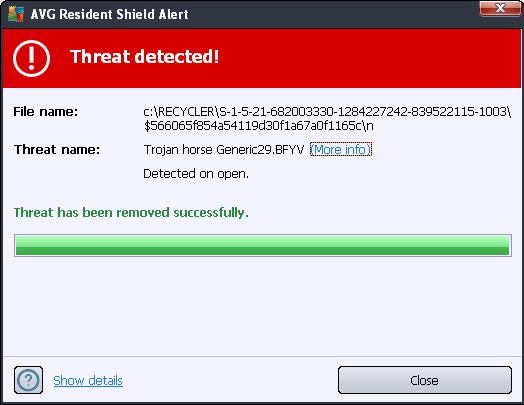
This may be, again a guess, the program that is hidden in the recycler directory that re-spawns the GAC\Desktop.ini file. Since code contained in the file "n" was a module used by explorer.exe ( which is running all the time) then the file "n" could be responsible for the constant attempts to contact the malicious websites and to re-spawn "desktop.ini" So for now, I appear to be clean - after a few more reboots - no more desktop.ini file and no more pop-ups from MBAM - telling me that a malicious site is being contacted. Next day - an update Well the very next day after I thought all was well - I got this message from my AVG program - see below: 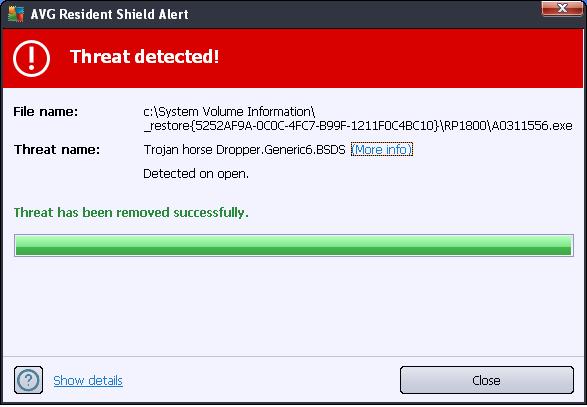
Nothing serious happened to my computer but this message means that some program was trying to open ( execute ) a trojan ( Dropper.Generic6.BSDS ) and AVG stopped it. So the attack vector program is apparently still around. So I ran a full scan (again) of AVG - and it found some more bad guys and cleaned them out. The point is, one can never really be sure all crapware was removed - I can never say with certainty that my computer is 100% clean. For now I just have to be extra vigilant. I guess that this is just one more annoyance one has to deal with after a serious trojan/virus attack. Maybe some day Microsoft will make a bullet proof operating system. |
 |
|






